The Freedom Kill Switch
Return to ENC 3241 Student Articles Menu

Abstract
Losing the ability to access the internet would create major problems in a developed nation that uses such technology, not only to enact business, but
also to provide emergency services to the public. Without the internet life as we know it would be greatly affected. With the recent unrest in the Middle East and the shutting down of the internet by the Egyptian government, many people are questioning whether or not it could happen in the United States. This paper takes a look at the political and technical aspects of this question and also covers new legislation and the history of shutting down the internet in other countries. The internet has been shut down in several countries in the past and today it is censored in varying degrees in most places, while access is non-existent in North Korea. Although technically it is getting more difficult to completely shut down the internet, people must be aware of political forces that may over-regulate. The most recent bill in Congress is being promoted as a way to protect the internet in case of a cyber-attack on necessary infrastructure. As technology moves forward the internet will be less prone to interruption, but more likely to be threatened by political enemies who want to control access to information.
Introduction
The United States’ core foundation is based in freedom; freedom to speak our minds, to not be squelched by the government, and to not have our rights and liberties taken away from us. The explosive growth and popularity of the internet has given new ways to exercise these liberties. In fact, the internet has become such an integral part of everyday life, for both personal and business purposes, that it would be nearly impossible for our country to function without it. Even though it is essentially a basic need for modern survival in the 21st century, many politicians have attempted to pass into law measures that would enable the government to restrict the internet inside, and outside, our borders. These attempts at restricting our freedoms, masked under the guise of security measures, are unconstitutional, and violate the ideals of what our founding fathers sought to protect. This is not a problem limited to just the US; several countries around the globe already have the ability to isolate themselves from the rest of the world. We have seen this happen on several occasions, and it always ends up drastically violating the freedoms of that country’s citizens.
In the past few years, there has been an exponentially increasing amount of attention on protecting the U.S. from cyber-threats; new vulnerabilities are created and need to be protected against as more and more individuals, companies, and government facilities are connected to, and rely upon, the internet. While there is a need to protect our country from cyber-attacks, the recent legislative actions have been intended to go beyond just protection, and instead are attempts at controlling the masses. We need to protect ourselves from true cyber-threats, but at the same time we need to ensure the government does not remove those rights on which our country was founded.
History of Internet Censorship and its Effects around the World
Online censorship has become big issue in the media as of late. By studying other countries and their history of censorship we can determine the effects that internet censorship has and will have on the global community and the laws that shape it. The following will state the concerns of what internet censorship can lead to, the way internet censorship has affected foreign countries in the past, and the issues that are affecting us at home.
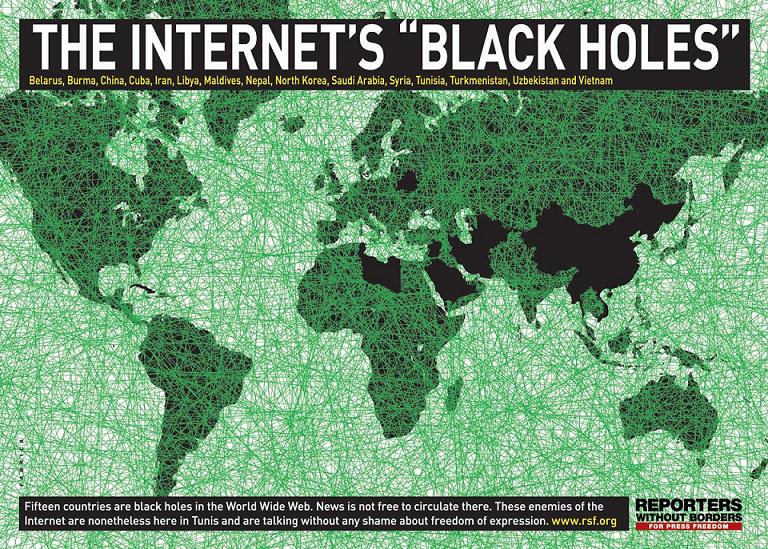
North Korea, a totalitarian state, has among the strictest regulation policies in the world. Internet access in North Korea is banned, and only a few top tanking officials have access to it. The North Korean people are isolated from the rest of the world and are kept in complete ignorance. It is one of the hardest places in the world to cover by the foreign press. Visas are only issued for sporting or other cultural events and are watched at all times (“North Korea”).
Similarly, China has regulations imposed to censor the internet and keep its people in a perpetual state of ignorance. Ever since the protests that occurred in Africa and the Middle East in 2011 the "Chinese government tightened its grip on electronic communications, and appeared to be more determined than ever to police cellphone calls, electronic messages, e-mail and access to the Internet in order to smother any hint of antigovernment sentiment" (“Internet Censorship in China”). In September 1996, China reportedly banned access to an estimated 100 Web sites by using a filtering system to prevent delivery of offending information. The banned sites included Western news outlets, Taiwanese commentary sites, anti-China dissident sites and sexually explicit sites. Since this time, China has enacted several highly restrictive laws that prohibit the publishing of political viewpoints that are undesirable to the Chinese government, as well as blocking foreign media and human rights websites (“Internet Censorship: Law & Policy”).
Egypt has been in the news lately because of the protests involving regime change. In late January of 2011, the websites Twitter and Facebook were blocked to slow protestors from being able to organize across the country. Soon after, the entire internet was shut down (Egypt). To place a ban on the internet is to place a ban on communication. Almost everyone in the 21st century communicates using the internet, whether it is through e-mail, social networking sites, or video chatting. Every person has the right to voice their opinions and be heard. The protests in Egypt raised many questions around the world of just how a single country can shut down the internet, and if it can happen in Egypt, could it happen in the United States? Because the internet has become such a global tool for communication and business transactions, such a shutdown left Egypt completely cut off from the online business world. It was surely a wakeup call for businesses around the world; if one country is affected then businesses worldwide would be affected. According to newspaper reports, the first five days of the shutdown cost the Egyptian government 90 million USD; a huge blow to the economy, especially in such a short time period (“Egypt Internet Shutdown”).
Also, consider the effect it has on financial institutions and IT providers. Many people will lose their jobs if a shutdown were to happen. At the very least, this presents the danger of giving the state too much power over communication and the internet.
Over the past couple years there has been talk about the United States putting restrictions on certain websites, and on September 20, 2010 the Combating Online Infringement and Counterfeit Act was introduced into Congress. If passed, this bill would give the government the right to blacklist any website that was "dedicated to infringing activities," as defined within the text of the bill (“Internet Censorship”). Although the bill was eventually killed, it is a reminder to the people that not all of their rights are guaranteed. People need to demonstrate that they are willing to fight for the rights that make this country so Free. History tells us that the only way for change to come about is for people to be informed as to what their country is doing to inhibit their citizens’ ability to access uncensored information. While this is relatively easy for most people, some places like China and North Korea make it almost impossible without any dire consequences for an individual to achieve. It is the responsibility of every citizen of a free state to make sure that the liberties of the people are not infringed upon.
Political Viewpoints around the Globe
In looking at the political viewpoints that control access to information via the internet there are two distinct groups that determine people’s experience. The industrialized nations are open, democratic societies that believe in freedom of speech and the open exchange of ideas, while many of the emerging and third world nations are either communistic or under the control of a dictator. It is these two groups that mark the difference of how much control is exercised over the internet, and whether the situation exists that the internet could possibly be shut down.
The recent political turmoil in Egypt has caused governments from all over the world to evaluate policies regarding the internet (“Reaching for the Kill Switch”). Political viewpoints concerning the internet in the United States can be broken down along the usual political divide of left vs. right, which has recently been focused on big government vs. small government. In this particular case, the left is on the side of government regulation and laws that provide the security to protect the internet from cyber-attacks, while the right believes that this can be better accomplished by the private sector, where businesses can respond quicker and more effectively, since they have a much better technical understanding of the issues than does the government (Currie). This situation has recently come to light with the proposal of a new bill in Congress, The Protecting Cyberspace as a National Asset Act of 2010, which allows the president authority to shut down certain sections of the internet in emergency situations (Politicol). The bill's authors tried to distance themselves from what's happened in Egypt, issuing a statement:
"Our bill already contains protections to prevent the President from denying Americans access to the Internet — even as it provides ample authority to ensure that those most critical services that rely on the Internet are protected" (Sutter).
Obviously, Americans who have been brought up on the belief that freedom of speech is an inalienable right fear any kind of censorship and believe that accessibility is paramount. This access is not only a political concern, because not only does a great deal of our business operate on the web, but so does local, state, and federal government agencies. In other words, our society can no longer function without the internet, or as a recent PC Magazine article states,
… the Internet would need to be shut down to prevent further damage to the country, which apparently can no longer function without the Net…The country can't function without the Net, so we need to secure the net, which includes having the ability to shut it down. But with the Net down, how can the country function? (Dvorak)
The global political landscape is a defining factor in how the handling of the internet is accomplished. As stated earlier, it is the difference between open and closed societies and how their governments treat the people that determines the amount of control. Dieber and Rohozinski, in their report Liberation vs. Control: The Future of Cyberspace, state that
“…liberal democracies remain engaged in a struggle against authoritarian value systems that are different from our own, and that this - not any inherent quality of the emerging means of communications - shapes the cyber battle space.”
It is these authoritarian value systems that feel they must control the information that is available to their people, and fear an uprising such as that which happened in Egypt. Although use of the internet to organize demonstrations is a major concern for many countries, it is the limiting of information that is the tool most often used by places such as China. Through filtering content, the Chinese government has been able to provide such a rich and diverse internet experience that the people do not know how much censorship is actually occurring.
As part of a networked authoritarian society, China’s 400 million Internet users are managing to have a lot more fun, feel a lot more free, and are a lot less fearful of their government than was the case even a decade ago. At the same time, thanks to homegrown engineering talent plus lots of help from American and European multinationals, the government has so far managed to keep tabs on enough people enough of the time, and censor and manipulate enough online conversations, that nobody has been able to organize a viable opposition movement (McKinnon, Schwartz).
It is fairly obvious that the political viewpoints of each country are a major threat to an open and easily accessible internet. While most citizens in the industrialized nations trust that their government will not hinder access to information, they must still remain vigilant with such issues as new laws to protect the internet from cyber-attack. In countries where citizens have fewer freedoms, they are at the mercy of their leaders as to how much information they can obtain through electronic means. As new technologies are developed, people will gain greater access and find ways to circumvent censorship. At the same time governments like China have found ways to deceive people into believing that their internet experience is an open one. In the past, these governments have found it easy to control the airwaves of television and radio, but it is becoming much more difficult to control information with today’s technology. More than any other factor, it is politics that determines whether or not the internet can be shut down in their country.

The U.S. "Internet Kill Switch" Bills
There have been several bills introduced relating to regulating the internet in creating an “Internet Kill Switch.” We can see an increasing amount of these legislative actions the most in recent years, due to the rise in popularity of the internet, and the integral role it plays in modern society. The most controversial bills are the Cybersecurity Act of 2009, The Protecting Cyberspace as a National Asset Act of 2010, and the Cybersecurity and Internet Freedom Act of 2011.
The first of these bills, S.773 - Cybersecurity Act of 2009, sought to give the President the ability to
“Order the limitation or shutdown of Internet traffic to and from any compromised… critical infrastructure information system or network” (“Cybersecurity Act”).
This bill was the first of many to be dubbed “The Internet Kill Switch.” After this bill was introduced in April of 2009, there was uproar of protest immediately following the introduction bill, from bloggers and news editors to civil rights groups and government officials, all worried about the impact this bill would have on civil rights, especially concerning the First Amendment. Under this bill, critical infrastructures are defined as
(A) Federal Government information systems and networks; and (B) State, local, and nongovernmental information systems and networks in the United States designated by the President as critical infrastructure information systems and networks. (“Cybersecurity Act”)
This bill gives the President the authority to declare that any equipment that is used in the “…control, display, switching, interchange, transmission or reception of data or information, and include computers and computer networks, ancillary equipment, software, firmware and related resources” (USC). If this bill would have passed, almost every single electronic device that exchanges information with another device could be deemed a critical infrastructure. A cyber-emergency is an emergency based on any matter “relating to, or involving the use of, computers or computer networks” and “any process, program, or protocol relating to the use of the Internet or an intranet, automatic data processing or transmission, or telecommunication via the Internet or an intranet” (USC). During a cyber-emergency, the government would be able to completely shut down all electronic communication and devices, even those located in private residences (including atomic clocks, televisions, most computers, cell phones, and even some refrigerators). Unconstitutional at its roots, this bill aimed to remove civil rights and liberties.
In March of 2010, the bill was rewritten to be more specific on the powers granted to the President, and removed the definition of a critical infrastructure. Under this revision, the President and various consultants would need to establish a procedure for designating any information system that “the infiltration, incapacitation, or disruption of which would have a debilitating impact on national security, including national economic security and national public health or safety” (“Cybersecurity Act”). Also, the President would have to develop a plan that would be enacted in response to a cyber-emergency, instead of being directly authorized by the bill to shut down the internet. Unfortunately, this is even worse, as there is no limitation to what the President would be allowed to incorporate into his plan, still gives the President the ability to enact his plan on his own, and allows the plan to include an “internet kill switch”. It does specify, though, that the power given to the President to declare a cyber-emergency, and put the response plan into motion, does not “authorize, and shall not be construed to authorize, an expansion of existing Presidential authorities” (“Cybersecurity Act”); however, even if it does not expand existing authorities, it does provide new ones. Thankfully, neither version of this bill was passed.
Senator Joe Lieberman introduced S.3480 - Protecting Cyberspace as a National Asset Act of 2010, and it too saw an overwhelming negative public response immediately following its introduction in June of 2010. It calls for the creation of a National Center for Cybersecurity and Communications; the NCCC would be ultimately responsible for designating what is and is not a critical infrastructure, as defined by the President and his consultants (“Protecting Cyberspace Act”). Just as the Cybersecurity Act of 2009 did not adequately define what would be considered a critical infrastructure, this revision is even less defining. A letter to Senators Lieberman, Collins, and Carper from the ACLU and other civil liberty groups, expressed their concern with how this bill does not offer protection against the infringement on civil rights, define what a critical infrastructure is, and does not include provisions to ensure only “truly critical network components” would be affected (Richardson). This bill does have many benefits over its predecessor. A cyber-emergency is redefined as when anyone or anything “…disrupts, attempts to disrupt, or poses a significant risk of disruption to the operation of the… critical infrastructure” (“Protecting Cyberspace Act”). Even though critical infrastructures are not explicitly defined, it does limit a cyber-emergency to only situations that affect critical infrastructures. The power to declare a cyber-emergency still resides with the President, but the emergency can only last at maximum 30 days, and no more than four consecutive months of cyber-emergencies can be declared, without approval by Congress. This bill also incorporates further checks and balances, limiting the actions taken by the President to those that are the least disruptive means possible, and provide guidelines that should be followed when developing threat responses. Ten days of this bill was introduced, Lieberman stated in an interview with CNN
“We need the capacity for the President to say: Internet service provider, we’ve got to disconnect the American internet from all traffic coming in from another foreign country” (Crowley). He further explains that the government should never take control over the internet, only that it should be able to block all internet traffic into, and out of, America. Lieberman also believes the U.S. government should be able to disconnect the internet just as the Chinese government currently can (Crowley).
We can see that Lieberman is not concerned with protecting the civil rights of Americans, and instead would like to see the same control on telecommunications that Egypt recently exerted over its people. The following video shows how President Obama disagrees with Lieberman, and urges China to loosen it's freedoms. This bill was not passed into law, and Obama remains a hero in the eyes of many Chinese citizens.
At some point in the 6 months following the introduction of S.3480, Lieberman radically changed his stance on government control of the internet. Now, Lieberman “would never sign on to legislation that authorized the President, or anyone else, to shut down the Internet. Emergency or no, the exercise of such broad authority would be an affront to our Constitution” even though that is exactly what he tried to achieve (“Statement on Cybersecurity”). This shift in principles coincides with the introduction of S.413 Cybersecurity and Internet Freedom Act, a revised version of S.3480. This bill, introduced in February of 2011, no longer defines, nor recommends, what should be considered a critical infrastructure, and instead adopts the definition used in the Patriot Act. This bill explicitly states that “neither the President, the Director of the National Center for Cybersecurity and Communications or any officer or employee of the United States Government shall have the authority to shut down the Internet” (“Bill on Serious Cyber Security Threats”). Unlike any previous bill, S.413 requires that every cyber-risk that this bill empowers the government to respond to must be explicitly defined to what the risk is, and to what critical infrastructures could be affected. If a risk is not on this list, or the threat that arises from a listed risk, but affects a non-listed critical infrastructure, this bill does not give the government the ability to respond to it. Even though this bill requires that the NCCC does not take any action that infringes upon any Constitutional Rights, it also prohibits judicial review by the courts, rendering an ineffective solution to the civil rights issue (Myth vs. Reality). This bill has not been voted on yet.
Proponents of these bills argue that there cannot be exact specifications as to every method of control given to the government to protect its country against cyber-attacks, because the internet and the technologies it relies upon are constantly changing (Crowley). Unfortunately, we have already seen the government abuse its power in policing the internet. In January of 2011, 84,000 websites were illegally seized by the Immigration and Customs Enforcement Agency for trafficking child pornography, even though none of the websites had anything to do with trafficking child pornography (Edelman). It is examples like this one that show just how little the government cares about its citizens’ rights, and proves the government will, without a doubt, abuse any unchecked power given to it. In their current state, these bills cannot provide the cyber-security that our country needs; instead we are given the choice between protecting ourselves from potential cyber-threats or protecting ourselves from our own government.
Technical Side Of The "Internet Kill Switch"

When you look at the more technical side of the internet, and how the internet is just one big mesh network, you’ll discover that shutting down the internet in a country is nearly an impossible task. A mesh network is kind of like a spider web. When one strand breaks, the other strands hold the web together. Now apply that to the internet, which the spider web represents. Each device connects to a local server, which connects to other servers and so on. They connect through cables, satellites, and mobile devices. So there are a lot of different kinds of pipelines to shut down.
The American government is working on a way to stop the internet if we happen to have something like a cyber-terrorism attack. This is something that we already deal with on some level already. There are constantly attempts on highly sensitive government organizations such as the CIA or the U.S. Power Grid. At a conference in New Orleans, information was disclosed by a senior analyst of the government stating that multiple power outages that had taken place in the country were due to cyber-attacks. This goes to show that we need a safety plan to stop any possible attacks in the near future. Some predict the next Pearl Harbor or 9/11 scale disaster will be related specifically to cyber terrorism.
In some countries such as Brahma, shutting down the internet is not too difficult to deal with due to the fact that the technology is not possessed by everyone. Also, the most important reason is there is only one internet service provider, or ISP. ISP is a supply line connecting to the World Wide Web. “In Egypt, they pulled the plug on the internet” (Zax, David. "Could Egypt Happen Here? ). Which was more difficult to contain as they had a much larger number of people with smart phones and computers along with five internet service providers. With simply a few changes to the provider’s routers, “changing some lines of code” (Lilly, Paul. "Maximum PC | How Egypt's Internet Kill Switch Works) there is no communication into or outside of the country. America has hundreds of different ISPs and nearly every citizen has some sort of internet device.
Border Gateway Protocol is what is used for ISPs to connect to each other across what are usually country borders. Bringing those down is another step to stopping the internet connection. Shutting these down can raise issues as the internet relies on all the countries networking each other together. A large portion of the internet doesn’t reside in the U.S. Websites are located on servers which reside all over the world.
With all that being said, Senator Joseph Lieberman has requested that the White House be given the capability to shut down a single website or maybe even a portion of the web. People are calling it the “Internet Kill Switch.” (Orlin, Jon. "In Search Of The Internet Kill Switch) Along with that comes legislation that will prevent the president from doing what Mubarak did: preventing his people from being able to communicate with the outside world.
How does the “Internet Kill Switch,” work when executed? Even though up to now there is nothing but a bill that keeps getting revised, the process would be overall the same. The president is alerted that there is a cyber-attack that is compromising sensitive data or infrastructures. Next he will declare what is being called a “Cyber Emergency,” which is what everyone is calling the “Internet Kill Switch” (no, it is not an actual switch that flips on and off). When this directive is issued, Homeland Security will immediately contain the situation.
Containing the situation is not as simple as shutting down the hundreds of ISP’s and Wireless Service Providers. That would be a very difficult task, and could not be completed within a few hours; it would take more like a few days at least. So in this case they would shut down ISPs called Tier 1. Tier 1 ISPs are the main service providers to all the smaller service providers. This would cause the most impact on internet connections in America as multiple ISPs are connected to each one. Another thing to shutdown would be the Internet Exchange points which are called “Carrier Hotels.” They are located around the country and would be much less difficult to shut down than all the ISPs. Even after all this, there are still possibilities of back door attacks and local attacks that haven’t been eliminated.
Basically, the best way to prevent these cyber-attacks is to start monitoring the internet, which many believe will be the end of privacy over the internet (even though privacy on the internet does not hold much meaning anymore). Developing standards for the internet seems to be the most preventive measures available. In this case deep internet packet sniffing would most likely become illegal, and there would be a new law enforcement branch in America. Constant monitoring of packets passed over the internet would be very common.
Conclusion
As the internet becomes more readily available to everyone across the globe, there is a need to protect the US against cyber-threats. The ability to anonymously affect a country from a computer halfway across the world is a relatively new phenomenon, and there is no single security measure that will completely protect our country without infringing upon the rights of its people. Our country is currently taking the first steps in creating the multi-faceted approach of the much needed cyber-security in our country, and it will be some time before all aspects of the issue are examined and attended to. We have already seen other countries completely cut off themselves from the rest of the world, and the negative implications on its citizens’ rights were disastrous. Whatever the solution becomes, we must ensure that it provides the much needed protection from cyber-threats and, almost more importantly, does not take away from what it means to be an American: to be treated fairly, equally, and the freedom to live without fear of our government.
Works Cited
44 USC Sec. 3532. 1994. Web. 6 Mar 2011. <http://uscode.house.gov/download/pls/44C35.txt>
"After Egypt, Will U.S. Get 'Internet Kill Switch'?" PC Magazine Online. Academic OneFile. Web. 24 Feb.
"China." Reporters Without Borders. Reporters Without Borders, n.d. Web. 26 Feb. 2011. <http://en.rsf.org/report-china,57.html>
Currie, Kelley. "The Battle Over Internet Freedom." The Weekly Standard. The Weekly Standard, 26 Oct 2010. Web. 24 Feb 2011. <http://www.weeklystandard.com/blogs/battle-over-internet-freedom_512987.html?page=1>
Crowley, Candy. Interview with Senator Joe Lieberman. State of the Union with Candy Crowley. CNN, Jun 20, 2010. Web. 15 Mar 2011. <http://www.cnn.com/video/#/video/politics/2010/06/20/sotu.lieberman.cyberwar.cnn?iref=allsearch>
Diebert, Ronald and Rafal Rohozinski. "Liberation vs. Control: the Future of Cyberspace." Journal of Democracy 21.4 (2010). Web. 24 Feb 2011. <http://www.journalofdemocracy.org/articles/gratis/Rohozinski-21-4.pdf>
Dvorak, John C. "Shutting Down the Internet." PC Magazine Online. Ziff Davis, 31 Jan 2011. Academic OneFile. Web. 24 Feb 2011.
Eddlem, Thomas. “Does the U.S. Have an Internet Kill Switch." New American Magazine 21 Feb 2001. Web. 24 Feb 2011. < http://www.thenewamerican.com/index.php/tech-mainmenu- 30/computers/6397-does-the-us-have-an-internet-qkill-switchq>
"Egypt." Reporters Without Borders. Reporters Without Borders, n.d.. Web. 26 Feb. 2011. <http://en.rsf.org/report-egypt,149.html>
"Egypt Internet Shutdown - How Will South Africa Be Affected In A Similar Scenario.” Ileadonline. Ilead Online, 14 Feb 2011. Web. 26 Feb. 2011. <http://www.ilead.co.za/blog/egypt-internet-shutdown-%E2%80%93-how-will-south-africa-be-affected-in-a-similar-online-shutdown-scenario.html>
"Internet Censorship." ACLU.org. American Civil Liberties Union, n.d. Web. Feb. 2011. <http://www.aclu.org/free-speech/internet-censorship>
"Internet Censorship in China." NYTimes. The New York Times, 22 Mar 2010. Web. 26 Feb 2011. <http://topics.nytimes.com/topics/news/international/countriesandterritories/china/internet_censorship/index.html>
"Internet Censorship: Law & policy around the world." EFA. Electronic Frontiers Australia, 28 Mar 2002. Web. 26 Feb. 2011. <http://www.efa.org.au/Issues/Censor/cens3.html>
“Lieberman, Collins, Carper Statement on Cybersecurity.” Senator Joe Lieberman. United States Senate, 1 Feb 2011. Web. 5 Mar 2011. <http://lieberman.senate.gov/index.cfm/news-events/news/2011/2/lieberman-collins-carper-statement-on-cybersecurity>
“Lieberman, Collins, Carper Introduce Bill to Address Serious Cyber Security Threats.” Senator Joe Lieberman. United States Senate, 18 Feb 2011. Web. 5 Mar 2011 <http://lieberman.senate.gov/index.cfm/news-events/news/2011/2/lieberman-collins-carper-introduce-bill-to-address-serious-cyber-security-threats>
Lilly, Paul. "How Egypt's Internet Kill Switch Works." Maximum PC. Future US, 31 Jan 2011. Web. 21 Mar 2011. <http://www.maximumpc.com/article/news/how_egypts_internet_kill_switch_works>
McKinnon, Rebecca and Bernard L. Schwartz. "Networked Authoritarianism in China and Beyond: Implications for Global Internet Freedom." Diss. Stanford University, 2010. Web. 15 Mar 2011. <http://rconversation.blogs.com/MacKinnon_Libtech.pdf>
"North Korea." Reporters Without Borders. Reporters Without Borders, n.d. Web. 26 Feb. 2011. <http://en.rsf.org/report-north-korea,58.html>
Orlin, Jon. "In Search Of The Internet Kill Switch." TechCrunch. AOL, 6 Mar 2011. Web. Mar 2011. <http://techcrunch.com/2011/03/06/in-search-of-the-internet-kill-switch/>
Politicol. "New Law to Shut Down the Internet." Politicol News. Politicol News Politics, 28 Jun 2010. Web. 24 Feb 2011. <http://www.politicolnews.com/obama-power-over-internet/>
"Reaching for the Kill Switch." The Economist. The Economist Newspaper Limited, 10 Feb 2011. Web. 24 Feb. 2011. <http://www.economist.com/node/18112043>
Richardson, Michelle. “RE: Civil Liberties Issues in Cybersecurity Bill.” CDT.com. Letter. 23 June 2010. Web. 24 Feb 2011. <http://www.cdt.org/files/pdfs/20100624_joint_cybersec_letter
.pdf>
Sutter, John D. "Could the U.S. Shut down the Internet?” CNN.com. Turner Broadcasting System, 3 Feb 2011. Web. 24 Feb 2011. <http://edition.cnn.com/2011/TECH/web/02/03/internet.shut.down/>
United States. Cong. Senate. Myth vs. Reality. By Collins, Susan M. and Joseph I Lieberman. 111th Cong, 23 Jun 2010. Wired.com. Web. 25 Feb 2011. <http://www.wired.com/images_blogs/threatlevel/2011/01/Myth-v-Reality.pdf>
United States. Cong. Senate. “Cybersecurity Act of 2009.” Washington: GPO, 2009. Web. 5 Mar 2011. < http://frwebgate.access.gpo.gov/cgi-bin/getdoc.cgi?dbname=111_cong_bills&docid=f:s773is.txt.pdf>
United States. Cong. Senate. “Protecting Cyberspace as a National Asset Act of 2010.” Washington: GPO, 2010. Web. 5 Mar 2011. <http://frwebgate.access.gpo.gov/cgi-in/getdoc.cgi?dbname=111_cong_bills&docid=f:s3480is.txt.pdf>
Zax, David. "Could Egypt Happen Here? Obama's Internet "Kill Switch." FastCompany. Mansueto Ventures, 28 Jan 2011. Web. 23 Mar 2011. <http://www.fastcompany.com/1721753/egypt-internet-kill-switch>
Lilly, Paul. "Maximum PC | How Egypt's Internet Kill Switch Works." Technology News, Computer and Notebook Reviews, Computer News, Computer Mods, PC News | Maximum PC. 31 Jan. 2011. Web. 21 Mar. 2011. <http://www.maximumpc.com/article/news/how_egypts_internet_kill_switch_works>
Orlin, Jon. "In Search Of The Internet Kill Switch." TechCrunch. Feb.-Mar. 2011. Web. Mar.-Apr. 2011. <http://techcrunch.com/2011/03/06/in-search-of-the-internet-kill-switch/>.
Zax, David. "Could Egypt Happen Here? Obama's Internet "Kill Switch" | Fast Company." FastCompany.com - Where Ideas and People Meet | Fast Company. Jan.-Feb. 2011. Web. 23 Mar. 2011. <http://www.fastcompany.com/1721753/egypt-internet-kill-switch>.









